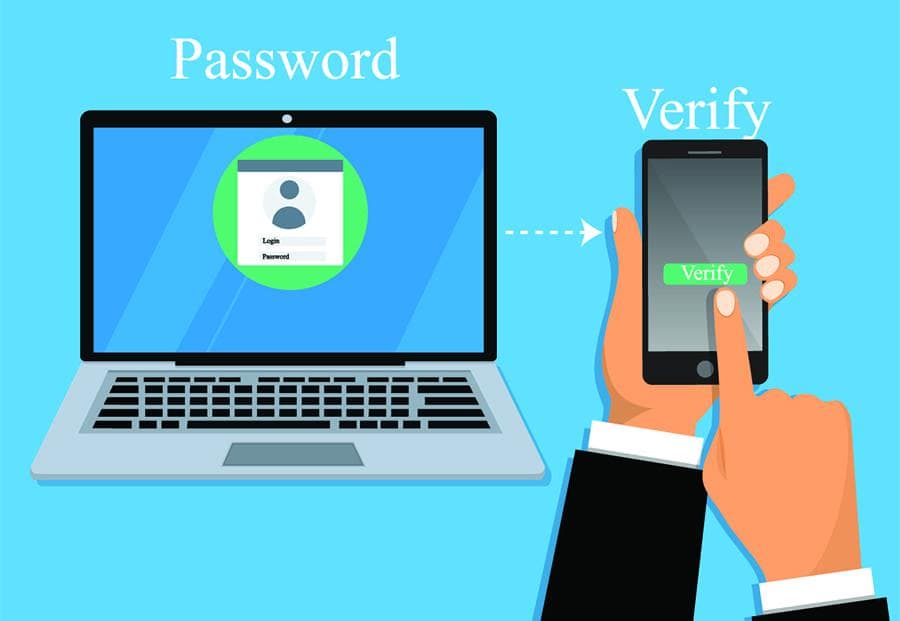
MFA (multi-factor authentication) or 2FA (two-factor authentication) is the same thing. These are security terms that represent an additional layer of login security for systems with valuable information such as Continue Reading
Digital Property Replacement is a subset of the Breach Rectification coverage of the cyber liability policy that PBI Group recommends. This section covers the replacement of software, data and hardware which has Continue Reading
If you missed or would like to watch/listen again here is the webinar recording with the presentation slides. Link to Presentation * Every coverage situation is different, and the final outcome depends on the unique Continue Reading
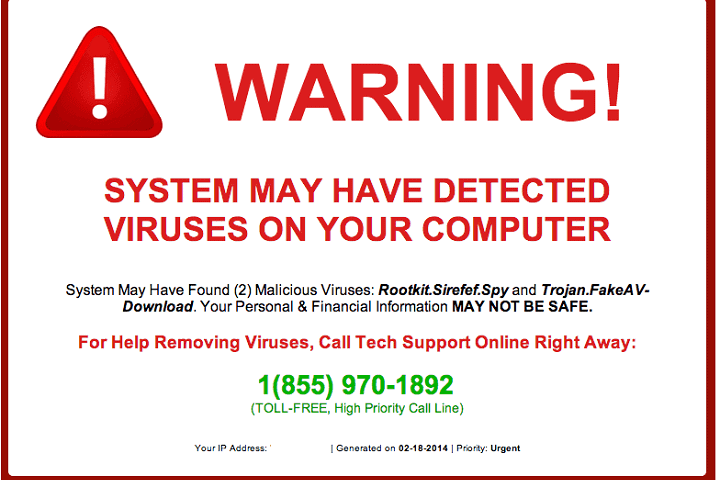
This scam is becoming more popular and can lead to your computer being further compromised by bad guys looking for more of your valuable client information. Be aware and don’t fall for this. Below is the Continue Reading
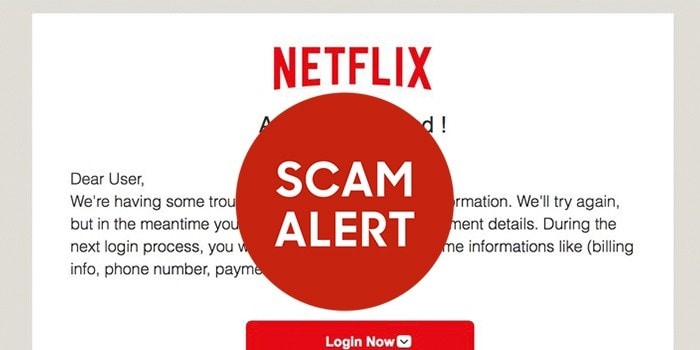
Phishing scams are very popular and often revolved around products or services which are important to us and widely used. Here is a successful scam that is going around this week, the bad guys are emailing you that Continue Reading
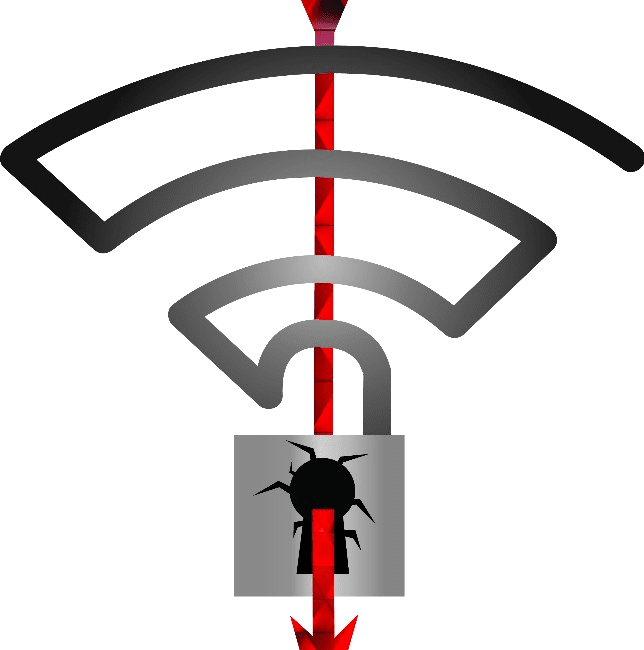
A new vulnerability has been discovered recently called “KRACK Attack”. In short, there is a exploitable flaw in the Wi-Fi security protocol WPA2, this protocol is designed to encrypts data traffic over Continue Reading
The bad guys are working hard, 100 attempts per month in Nevada! Our cyber liability policy cover for this type of claim. Get a quote today.Continue Reading
If so, you may be in a situation where your policy does not provide coverage due to an unsupported software application running on your computers. All software eventually reaches a point where it is no longer Continue Reading
If your systems are down due to a Ransomware attack, Business Interruption coverage can help by protecting your agency from loss of your income and additional expense when the Insured Computer System sustains a Continue Reading
You may have seen the news this weekend. Criminal hackers have released a powerful strain of ransomware that spreads itself automatically across all computers in a network, causing a global epidemic. If you are not Continue Reading
I, < Agent> will never request or forward alone someone else’s request * to my Client, via any form of electronic communication including email, text message or voice mail asking to transfer any funds. Continue Reading
Let’s first define the difference: Funds Transfer 1st Party coverage for Cyber Liability protects the Insured aka the real estate firm who holds the insurance policy from a loss of their own assets. A popular Continue Reading
A Data Breach Coach is a leader, often a person at a law firm, who is your main point of contact once a breach is suspected. He or she is available through a feature in your Cyber Liability policy via a 24-hour Continue Reading
Like a shield wall for an army, Security Awareness Training is a valuable tool to help reduce your cyber liability exposure by employing a formal process of educating agents regarding cybersecurity threats. The Continue Reading
Here is a good example of Deceptive Funds Transfer is it is explained in this Claims Scenarios from Victor O. Schinnerer & Company, Inc.: http://schinnerer.com/cyber/deceptive-transfer-insurance/Continue Reading
Social engineering is the art of manipulating people so they give up valuable information. Criminals use this tactic as it is easier to exploit the natural inclination to trust than to breach system security. Continue Reading